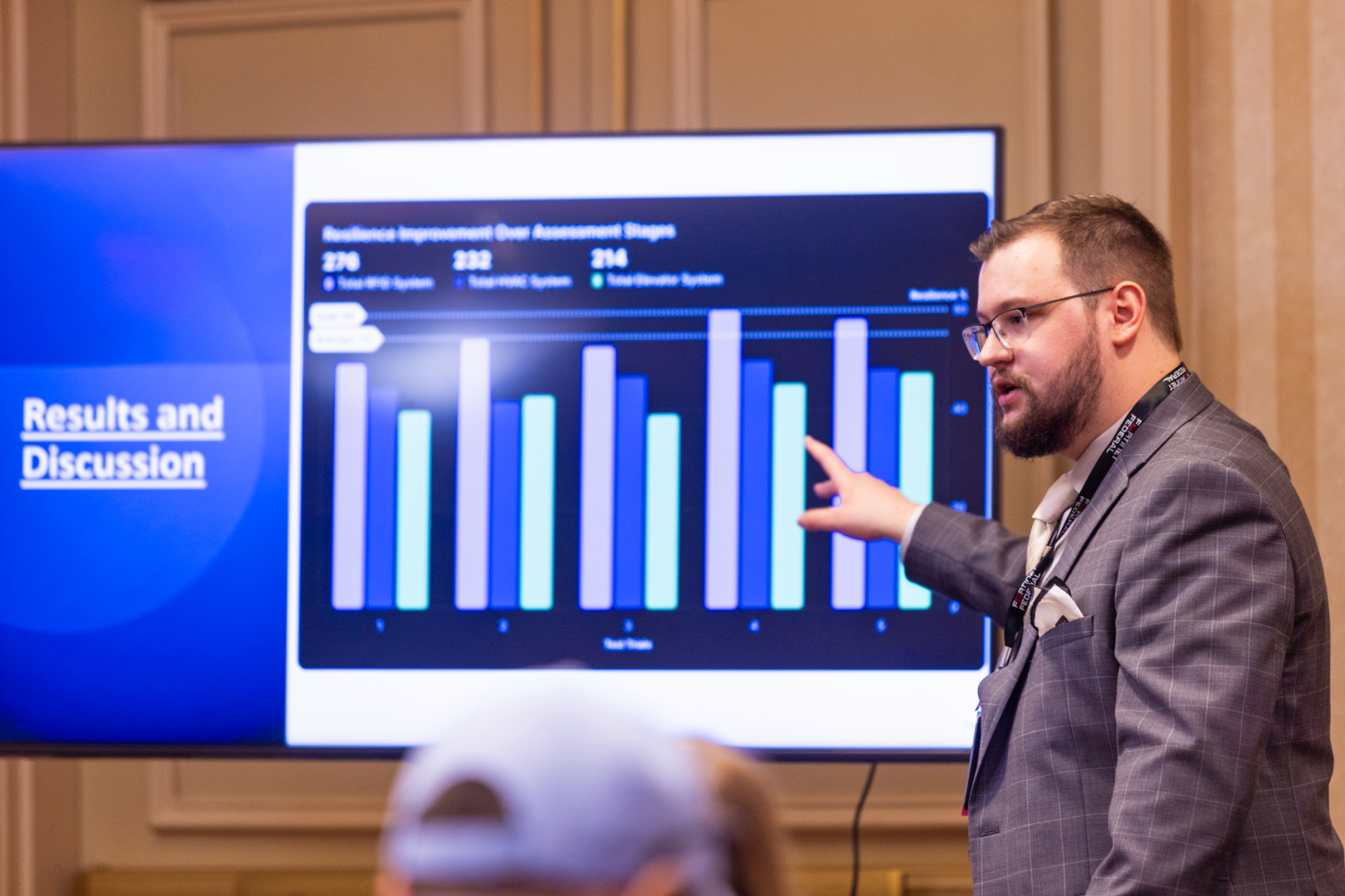
Research
In line with Augusta University's mission to become a top-tier research institution, School of Computer and Cyber Sciences faculty members are conducting research to stay one step ahead of today's ever-changing, technology-driven society.
Research is a central component of both our new Computer and Cyber Sciences PhD program and the thesis track of the MS, Computer Science program. In addition, with most of our faculty pursuing research, there is an excellent opportunity for undergraduate students to apply their knowledge from the classroom to create solutions in each of our research faculty's research foci. The Computer Science Colloquium Series, held on Fridays, offers students an opportunity to learn about cutting-edge research subjects in the areas of Computer Science, Information Technology and Cybersecurity.
Contact Us
School of Computer and Cyber Sciences
Summerville Campus
706-721-1110
Major Research Areas

Distributed and Parallel Computing

Security and Privacy

Formal Methods, Software Engineering and Programming Languages

Information Systems

Cyber-Physical, IoT, and Edge Systems

Artificial Intelligence, Machine Learning, and Data Science
Invest in the Future
Your investment in the School of Computer and Cyber Sciences directly fuels the next generation of technology leaders. By contributing, you empower us to provide a cutting-edge education in the critical, future-forward industry of computer science, information technology and cybersecurity, ensuring our students are equipped to tackle the complex challenges of the digital age.